Listen to me, and listen to me good. The most valuable commodity on planet Earth isn’t gold, it isn’t oil, and it sure as hell isn’t the paper money in your wallet. It’s data. Your data. And for the last twenty years, you’ve been giving it away for free like a chump. The conversation about privacy in Web3 isn’t some tech-nerd fantasy; it’s the single biggest power shift of our generation. It’s about taking back the keys to your own kingdom.

While the sheep are scrolling through their feeds, oblivious, a revolution is happening. A revolution that separates the new kings from the digital peasants. This isn’t just about hiding your Browse history. This is about wealth, power, and sovereignty. This is about you finally getting paid what you’re worth. So, pay attention. What I’m about to tell you could be the most important lesson you ever learn.
🕵️♂️ Web2: The Digital Cage They Built for You

How Big Tech Got Rich Selling Your Secrets
You think those social media platforms are free? That’s the biggest lie ever sold. You’re not the customer; you’re the product. Every click, every like, every private message you’ve ever sent has been logged, analysed, and sold to the highest bidder. These Web2 behemoths—the Googles, the Facebooks, the Amazons—they built trillion-dollar empires on the back of your life. They know who you vote for, what you buy, who you’re sleeping with. They know you better than your own mother. And they use that information to manipulate you, to sell you things you don’t need, to shape your thoughts. It’s the greatest hustle in history, and you’ve been the mark from day one.
The “Free” Lunch That’s Eating You Alive
They gave you convenience. They gave you shiny apps and endless content. And in return, you handed them the keys to your entire digital existence. You signed their terms and conditions without reading a single word—a contract that essentially made them your digital overlords.

They created a system, a digital panopticon, where your every move is monitored. This isn’t a bug in the system; it’s the entire business model. It’s a cage with invisible bars, and you willingly walked right into it.
Waking Up to the Manipulation Game
The name of the game is control. By centralising all this data, they created single points of failure, making them prime targets for hackers and government spies. Your most sensitive information is sitting on a server somewhere, a ticking time bomb waiting to be exploited. You feel that creeping sense of unease? That feeling that you’re being watched? That’s not paranoia. That’s your survival instinct kicking in. It’s telling you that the game is rigged, and it’s time to flip the table.
🚀 Web3: Your Escape Route to Digital Sovereignty

What is Web3, and Why Should You Give a Damn?
Web3 is the sledgehammer that shatters the digital cage. It’s the next evolution of the internet, built on the bedrock of decentralisation. What does that mean in plain English? It means there’s no central boss. No Big Brother. No CEO who can decide to sell your data or delete your account on a whim. Power is taken from the corporations and handed back to the people. It’s a network owned by the users, for the users. It’s your escape route. It’s your declaration of independence.
Seizing the Throne: Self-Sovereign Identity (SSI)
In the Web2 world, your identity is a collection of usernames and passwords controlled by a dozen different companies. In Web3, you have Self-Sovereign Identity (SSI). Your identity is yours, and yours alone.
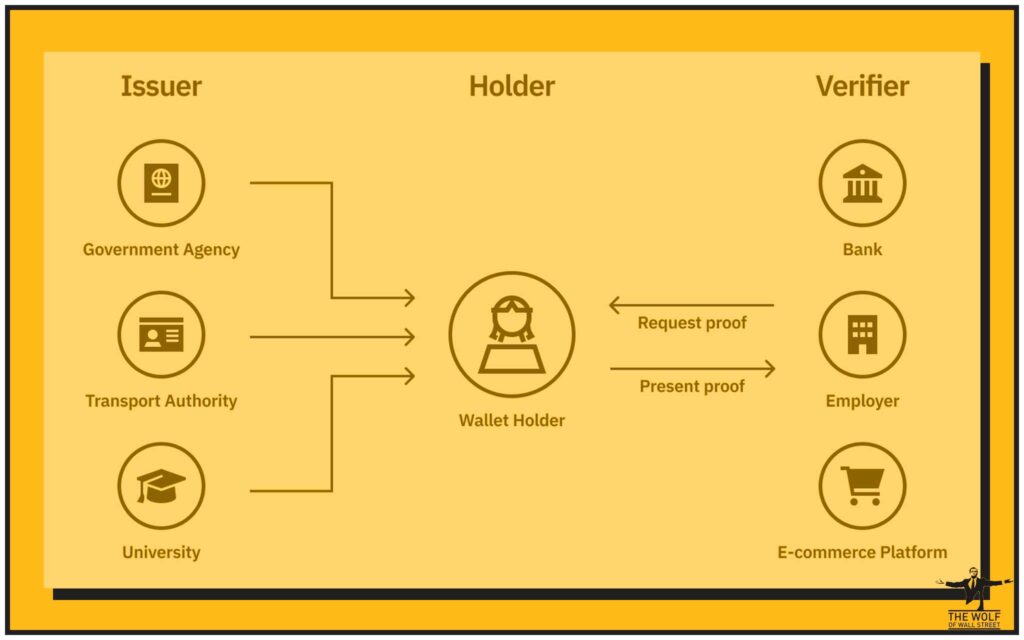
You hold the cryptographic keys, and you decide—with granular precision—what information you share, with whom, and for how long. It’s the difference between asking for permission and granting it. It’s the difference between being a subject and being a king.
Your Keys, Your Kingdom: The Power of Public and Private Keys
This entire kingdom is secured by something beautifully simple: keys. You have a public key—like your bank account number—that you can share with anyone. And you have a private key—the password to your vault—that you protect with your life. This simple cryptographic pairing is the foundation of your power. Lose your private key, and you lose everything. Protect it, and you are untouchable.
Decentralised Identifiers (DIDs): Your New Passport to the Digital World
Think of a Decentralised Identifier (DID) as your passport for the Web3 world. It’s a globally unique, verifiable identifier that you own and control. It doesn’t live on a corporate server; it lives on the blockchain. When you need to prove your age to enter a website, you don’t show your entire driver’s license anymore. Your DID allows you to prove just that one fact—”Yes, I am over 18″—without revealing your name, your address, or anything else. It’s total control.
🔐 The Arsenal: Advanced Cryptography for the Modern Wolf

Zero-Knowledge Proofs: Proving You’re a Player Without Showing Your Hand
This is where it gets beautiful. Zero-Knowledge Proofs (ZKPs) are the ultimate power move. They allow you to prove a statement is true without revealing the information that makes it true. It’s like telling someone the secret password to a club without ever speaking the password out loud. You can prove you have enough money for a trade, prove your identity, or prove your right to access something, all without ever exposing the underlying data. It’s the art of revealing nothing but proving everything.
Ring Signatures & Mixers: Covering Your Tracks Like a Pro
On a public blockchain, every transaction is visible. That’s a problem. But with tools like ring signatures, your transaction gets mixed in a group with others, making it impossible to tell who the real sender was. It’s like leaving a crowded room—no one knows which person dropped the note. Mixers take this a step further, tumbling your crypto with others to break the on-chain link. It’s digital money laundering for the good guys, ensuring your financial history remains your business.
Secure Multi-Party Computation: The Ultimate Trust Machine
Listen, trust is for suckers. In this world, you build systems that don’t require it. Secure Multi-Party Computation (MPC) allows a group of people to compute a result based on their combined private data, without any single person ever having to reveal their own data to the others. Think of it as a board meeting where everyone can vote on a secret number, and the final sum is revealed without anyone knowing how the others voted. It allows for collaboration and decision-making on a level of security that was previously science fiction. This isn’t just theory; you can learn more about its application in our guide on Multi-Party Computation.
💎 The Dream vs. The Gritty Reality
The Upside: Absolute Power and Control Over Your Data
The promise of Web3 is nothing short of revolutionary. It’s a world where you own your data. You control your digital identity. You move through the internet with a newfound sense of security and autonomy. The power to monetise your own data—or to keep it completely private—is placed firmly back in your hands. This is the dream.
The Downside: The All-Seeing Eye of the Public Ledger
But don’t get it twisted. This is not a privacy utopia… yet. Most blockchains, like Bitcoin and Ethereum, are public ledgers. Every transaction is recorded and visible to anyone. While your real name isn’t attached, your wallet address is. And that’s where the problem starts.
Why Pseudonymity Isn’t Invisibility
Operating under a pseudonym is like wearing a mask at a party. It offers a layer of protection, but a determined analyst can still figure out who you are. By linking your transaction patterns, connecting your address to a centralised exchange where you verified your identity, or using other advanced forensics, they can rip that mask right off. Never, ever mistake pseudonymity for true anonymity.
Smart Contract Loopholes: The Backdoors You Don’t Know About
The smart contracts that power decentralised applications are just code. And code can have bugs. Malicious actors and brilliant hackers are constantly probing these contracts for exploits and vulnerabilities. A single flaw in the code could lead to a catastrophic privacy breach or a total loss of funds. You have to be vigilant. You have to do your due diligence.
🏛️ The Wild West: Navigating the Regulatory Minefield

The Global Power Play: Regulation is Coming, Ready or Not
The governments of the world are waking up. They see this power shift, and frankly, it scares them. Regulations are coming, and they’re coming fast. Some countries are embracing the change, creating clear legal frameworks. Others are trying to strangle it in its crib. This regulatory battle is the new front line, and the outcome will determine the future of digital freedom. To stay on top, you need to understand the new rules of engagement laid out in things like the Crypto AML Guide.
The US Regulatory Maze: A Recipe for Confusion and Lost Opportunity
The United States, in its infinite wisdom, has created a chaotic mess. Different agencies are fighting for turf, issuing contradictory guidance, and creating a climate of fear and uncertainty. This isn’t leadership; it’s a disaster that stifles innovation and pushes talent offshore to places with clearer rules, like those laid out in the Liechtenstein Blockchain Act. Navigating this maze requires skill, insight, and nerves of steel.
🐺 The Wolf’s Playbook: How to Protect Your Assets in Web3

The Buck Stops With You: The Heavy Crown of Responsibility
In Web3, you are the bank. You are the security guard. You are the CEO of You, Inc. This incredible power comes with incredible responsibility. There is no customer service number to call if you get hacked. There is no “forgot my password” button for your private keys. The responsibility is entirely on you. You either step up and become a wolf, or you get eaten by them.
Dodging the Bullets: Phishing, Rug Pulls, and Scams
The space is flooded with sharks who want to take your money. They’ll use sophisticated phishing scams, promising you a fortune only to drain your wallet. They’ll launch projects, pump up the price, and then disappear in a “rug pull,” leaving you with worthless tokens. You need to be cynical. You need to be paranoid. Question everything. Trust no one.
The Critical Choice: Self-Custody vs. Centralized Crypto Cards
The most critical decision you’ll make is how you store your assets. Do you keep them in a self-custody wallet where you, and only you, hold the keys? Or do you trust a third party? Each has its trade-offs between convenience and security. Understand them intimately. Your financial future depends on it.
The Importance of a Solid Wolf Pack

Navigating this market alone is financial suicide. You need a pack. You need a community of killers who are in the trenches every single day, separating the gold from the garbage. You need a team that gives you the tools, the analysis, and the signals to make winning moves.
This is where you stop guessing and start executing. The The Wolf Of Wall Street crypto trading community is your unfair advantage.
- Exclusive VIP Signals: Stop gambling. Get proprietary signals designed to maximise your profits.
- Expert Market Analysis: Let seasoned traders tell you where the market is going, not where it’s been.
- Private Community: Network with over 100,000 other wolves. Share insights, strategies, and win together.
- Essential Trading Tools: Use volume calculators and other resources to make cold, calculated decisions.
- 24/7 Support: Never trade alone. Our team is always there to back you up.
Stop being the sheep. It’s time to become the wolf.
- Visit our service: https://tthewolfofwallstreet.com/service
- Join our Telegram community: https://t.me/tthewolfofwallstreet
📈 The Future is Unwritten: What’s Next for Web3 Privacy?

The Next Frontier: From IP Tracking to Content-Based Networks
The game is always evolving. Even in Web3, your IP address can be a weak link, potentially deanonymizing you. The next frontier is moving away from tracking who you are (IP-based) to focusing only on what you want (content-based). This is the holy grail—a truly private, efficient, and censorship-resistant internet.
The Knowledge Gap: Why Education is Your Sharpest Weapon
The single biggest threat to your success and security in Web3 is ignorance. The technology, the risks, the opportunities—they are all moving at lightning speed. You must commit to continuous learning. Read, watch, ask questions, and never, ever assume you know it all. The moment you get complacent is the moment you get wiped out.
Conclusion: Seize Your Digital Destiny or Get Left Behind
We stand at a crossroads. Behind us is the old world of Web2—a world of digital serfdom where you were the product. Ahead of us is the world of Web3—a world of sovereignty, control, and unprecedented opportunity. The tools are there. The technology is real. But it demands more from you. It demands vigilance, responsibility, and a killer instinct.

You can either stay in the cage they built for you, or you can pick up the sledgehammer and shatter it to pieces. The choice is yours. But make no mistake, mastering your privacy in Web3 is the first and most critical step to seizing your digital destiny.
❓ Frequently Asked Questions (FAQs) for Aspiring Wolves
Is Web3 actually 100% private and anonymous?
No. Not yet. Think of it as a spectrum. It offers vastly superior privacy tools and potential compared to Web2, but it’s not an invisibility cloak. Public blockchains are transparent, and mistakes can get you identified. True anonymity requires discipline and the right tools.
What’s the first, most crucial step to protect my privacy in Web3?
Get a hardware wallet. Immediately. Before you do anything else. This takes your private keys offline, making them nearly impossible for hackers to steal. Your keys, your crypto. Not your keys, not your crypto. It’s that simple.
What’s the biggest mistake rookies make with their privacy in crypto?
Reusing wallet addresses and connecting their “degen” wallet (where they make risky plays) to a centralised exchange where they’ve submitted their ID. That’s like leaving a direct trail of breadcrumbs from your secret activities right to your front door. Use different wallets for different purposes. Be meticulous.
Are Decentralised Identifiers (DIDs) the real future of online identity?
Absolutely. They represent a fundamental shift from corporate-controlled identities to user-owned identities. It will take time for mass adoption, but the concept is too powerful to ignore. It’s the difference between renting your identity and owning it outright.



