Right, listen to me, and listen to me good. The only thing standing between you and a life of mediocrity is action. You’re here because you need to recover access to a crypto account protected by two-factor authentication (2FA), and I’m here to tell you how to kick that digital door down and take back what’s yours.

You thought you were smart, didn’t you? Setting up 2FA, adding that extra layer of security. You were right. That was a boss move. But now you’re on the wrong side of the velvet rope, staring at your own fortune through bulletproof glass. Your phone is a brick, your authenticator app is a ghost, and every failed login attempt is another nail in the coffin of your crypto dreams.
Panic is a sucker’s game. It’s for the sheep who sell at the first dip and cry when they miss the pump. You are not a sheep. You’re a lion. And a lion doesn’t whimper; it roars. It hunts. It takes what it wants. This guide isn’t a gentle suggestion; it’s your playbook. It’s the set of keys to your kingdom. Read it, memorise it, and execute it with the ferocity of a trader closing a seven-figure deal. Because right now, the most important trade of your life is getting back into your own damn account. Let’s get to work.
📈 The Cold, Hard Reality of 2FA Lockouts
Let’s get one thing straight. Two-factor authentication is a weapon. In your hands, it’s a shield that protects your empire from hackers and thieves. But if you mishandle it, that same weapon can turn on you, locking you out of your own vault. The market doesn’t wait for you to find your lost keys. Every second you’re locked out is an opportunity squandered, a profit missed.

Why Your Greatest Strength is Your Biggest Weakness
You built a wall to keep the barbarians out. I respect that. It shows foresight. But what you failed to do was build yourself a private gate. You relied on one single point of entry, and now that entry is compromised. Amateurs think security is about building one impenetrable wall. Professionals—the real wolves—know it’s about creating multiple, secret access points that only they control.
The Illusion of Total Security
There is no such thing as a 100% foolproof system. None. Not on Wall Street, not in crypto, not anywhere. The moment you believe you are totally secure is the moment you become vulnerable. You got complacent. You set up your 2FA and thought, “Job done.” Wrong. The job is never done. Security is a process, a constant state of vigilance. You let your guard down, and the system did exactly what it was designed to do: it locked down at the first sign of trouble. The trouble is, the trouble was you.
The Million-Dollar Mistake Amateurs Make
The biggest mistake, the one that separates the whales from the minnows, is failing to plan for failure. You planned for an attack from the outside, but you didn’t plan for a screw-up on the inside. You lost the device, dropped the phone, or simply forgot the process. You didn’t save the backup codes. You didn’t write down the recovery phrase. This is the amateur hour mistake that costs people fortunes. Today, you learn to think like a professional.
💰 Your First Move: The Backup Code Blitz
Before you start crying to customer support or throwing your laptop out of the window, you make the first, most logical move. You use the lifeline the platform threw you when you signed up. I’m talking about backup codes.
The Lifeline They Handed You
When you enabled 2FA, the platform—be it Coinbase, Binance, or any other exchange worth its salt—showed you a list of single-use backup codes. They told you to save them. They practically begged you. These codes are your “get out of jail free” card. They are designed for this exact scenario. Your first move is to find where you stored them. If you can’t find them, you didn’t take this seriously enough.
How to Use Backup Codes Like a Pro
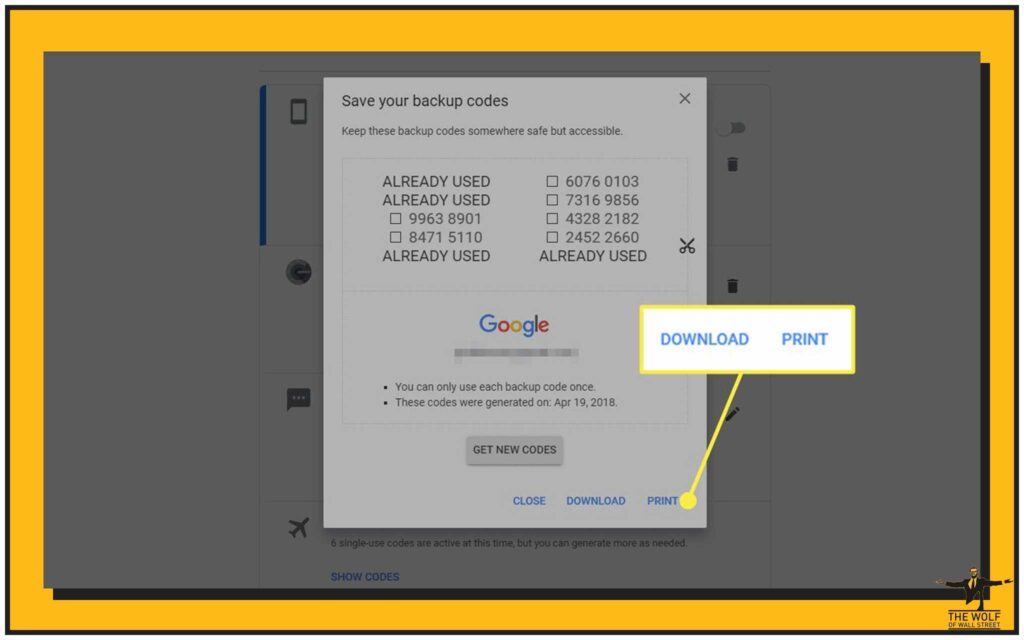
This is simple. Don’t overthink it.
- Go to the login page.
- Enter your email and password.
- When the 2FA prompt appears, look for a link that says “Use a backup code” or “Having trouble?”
- Click it. A field will appear.
- Enter one of your backup codes. Just one.
- You’re in.
The second you’re in, you don’t celebrate. You don’t go and check your portfolio. You go straight to your security settings and disable the old 2FA. Then, you immediately set up a new one and save the new set of backup codes like your life depends on it. Because in the crypto world, it does.
What If You Dropped the Ball?
If you’re reading this and you have a sinking feeling because you never saved those codes, then you messed up. Simple as that. You gambled and you lost this hand. But this isn’t the whole game. It just means we move to tactic number two. Don’t waste time beating yourself up. Acknowledge the mistake, burn the lesson into your brain, and move on to the next play.
📸 The “Show Me Your Face” Gauntlet: Identity Verification
Alright, so the backup codes were a bust. You were sloppy. Fine. Now you have to prove who you are. The platform has your money, and they’re not going to just hand it over because you asked nicely. You need to go through the identity verification process. This is non-negotiable.

When You Have No Other Cards to Play
This is your last resort before begging customer support. The automated account recovery process is your ticket back in. It’s designed to be rigorous. It’s designed to stop the very scum who might be trying to steal your assets. So, you will play their game, and you will win.
The Step-by-Step Playbook for Platforms like Coinbase
They all follow a similar script. Listen up.
- Start the login process. When you hit the 2FA wall, find the link for account recovery. It’ll be labelled “Need help?” or “Try another way.”
- The system will initiate the recovery protocol. It’s going to ask for proof.
- Upload Your ID: You will need a crystal-clear photo of your government-issued ID. A driver’s licence or passport. No blurry photos, no glare. Use a scanner if you have to. Act like a professional.
- Take a Selfie: The system will then activate your camera and ask for a live selfie or a short video. It uses biometric data to match your face to the photo on your ID. Make sure you’re in a well-lit room. Do exactly what it says—turn your head, blink, whatever it asks. Don’t be cute. Just execute.
The Waiting Game: How Not to Sweat It
You’ve submitted your proof. Now, you wait. The platform will tell you this can take 24-72 hours. For you, this is agony. Every minute feels like an hour. But you will remain calm. You will not bombard them with emails. You’ve made your move, and now you let the system work. They are reviewing your case, matching your data, and ensuring you are who you say you are. This delay is a security feature, not an inconvenience. Use this time to think about how you’re going to build a fortress around your account once you’re back in.
🚪 The Backdoor Strategy: Still Logged In?
Are you still logged into your account on another device? A phone, a tablet, an old laptop? If the answer is yes, stop reading this article and go to that device right now. This is a golden window of opportunity, and it is closing with every second you waste.
The Window of Opportunity is Closing—Fast
Being logged in somewhere is the ultimate backdoor. You have authenticated access. The system trusts that device. You can bypass the entire recovery nightmare by acting decisively from within the castle walls. Don’t log out. Don’t clear your cache. Don’t do anything except move to the next step.
Seizing Control Before It’s Too Late
Navigate directly to your account settings. Find the “Security” or “Login & Security” tab. This is your command centre. Inside, you will see your active 2FA method. This is the enemy. Your mission is to remove it and replace it.
Resetting Your 2FA from the Inside
Look for the option to “Change” or “Remove” your 2FA method. The platform will likely ask for your password one more time to confirm it’s you. Enter it. It will then allow you to disable the problematic 2FA. Do it. But you are not done. The second it’s disabled, you are vulnerable. You immediately enable a new 2FA method. Not later. Not tomorrow. Now. Get a new authenticator app, generate the new QR code, and this time, for the love of money, save the damn backup codes. While you’re at it, mastering the concepts behind public and private keys is fundamental knowledge that separates the rich from the poor in this game.
📞 Calling in the Cavalry: When to Escalate to Support

If the automated systems have failed you, or if your situation is a complete disaster-class mess, it’s time to get a human on the line. But you don’t go to them with your tail between your legs. You go to them with authority.
Don’t Be a Hero, Be a Winner
Trying to solve an impossible problem by yourself is foolish. The richest people on the planet have teams. Customer support is your temporary team. Your job is to use them effectively to get the result you want.
How to Talk to Support to Get What You Want
Be clear, be concise, and be firm. But be polite. These people hold the keys. You don’t threaten; you explain.
- “Hello, my name is [Your Name]. My account email is [Your Email].”
- “I have been locked out due to a lost 2FA device. I have already attempted the automated identity verification process, and it was unsuccessful. My case number is [if you have one].”
- “I need to escalate this case to regain access to my account. I am prepared to provide any and all information required to verify my identity.”
No emotion. No sob story about the trades you’re missing. Just the facts. You are a professional with a technical problem that needs solving.
The Information You MUST Have Ready
Before you even think about contacting them, gather your arsenal.
- Your full name and email address.
- The phone number associated with the account.
- The approximate date you opened the account.
- The source of funding (which bank did you use?).
- The amounts and dates of your last few transactions.
- The device and IP address you usually log in from.
The more high-quality information you can provide instantly, the faster they can help you. You’re making their job easier, which makes them want to resolve your issue faster. It’s a transaction. Give them what they need, and they will give you what you want.
🛡️ Fortress Protocol: Securing Your Account After Recovery
Getting back in is just the first half of the battle. Now, you ensure this never, ever happens again. Complacency is the enemy. From this moment on, your personal security is your religion.
You Got Back In. Now, Make It Impenetrable.
Your account was breached by your own error. That’s a brutal pill to swallow, but swallow it you must. Now you rebuild. You don’t just patch the hole; you build a fortress. For serious traders, understanding the landscape of crypto AML compliance and security isn’t just smart, it’s essential.
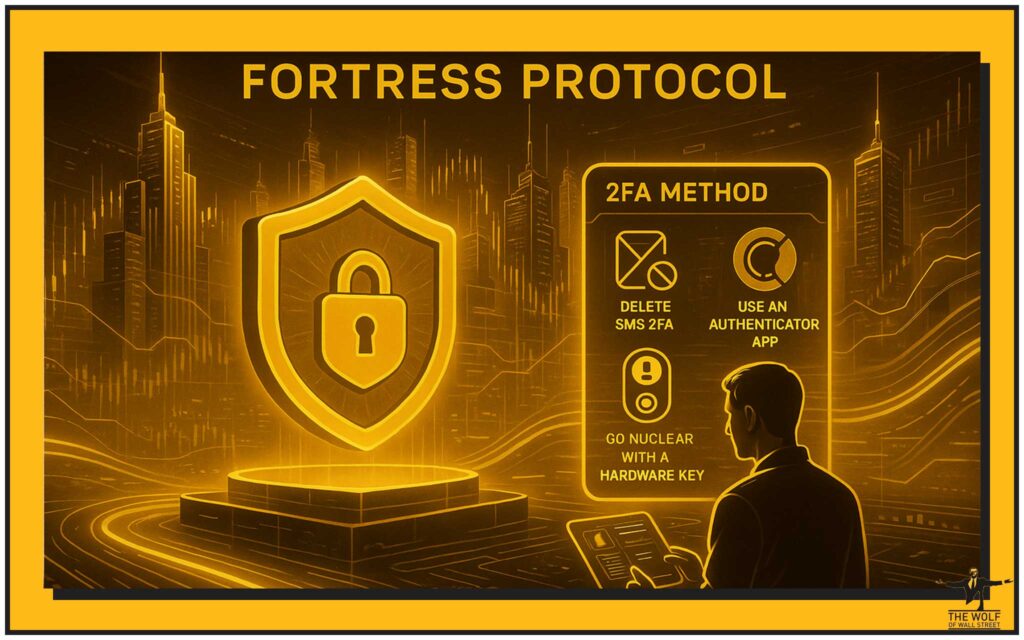
Upgrading Your 2FA Method (The Non-Negotiables)
- Delete SMS 2FA: If you are still using SMS for authentication, you are a sitting duck for a SIM swap attack. Stop it. It’s for amateurs.
- Use an Authenticator App: Download Google Authenticator or Authy. Authy has the advantage of cloud backups, which can save you from this exact mess in the future.
- Go Nuclear with a Hardware Key: For serious money, you buy a hardware key like a YubiKey. This is a physical device. Without it, no one gets in. It’s the gold standard.
Creating Redundancies So This Never Happens Again
- Store Backup Codes Properly: Print them out. Store a copy in a safe at home. Store another copy in a safe deposit box. Give a sealed envelope to a trusted family member. This is not overkill; this is wealth preservation.
- Review Your Settings: Every month, you do a security audit. Check your recovery email, your phone number, and your trusted devices. Stay vigilant.
- Consider Advanced Options: Are you holding six or seven figures? It’s time to think about a multisignature wallet. This requires multiple keys to authorise a transaction, making you a much, much harder target.
💀 The Point of No Return: Non-Custodial Wallets
I need you to listen to me very carefully. Everything we’ve discussed so far applies to custodial platforms like Coinbase, where a central company holds your crypto for you. If you are using a non-custodial wallet (like MetaMask or a hardware wallet) and you lose both your 2FA and your seed phrase, it’s over.
The One Scenario Where You’re Truly Screwed
In the world of self-custody, you are the bank. There is no customer support to call. There is no identity verification process. The seed phrase is the master key to everything. If that is gone, along with your device and any backups, your funds are gone forever. Burned. Sent into the digital void, inaccessible to anyone for all of eternity.
Why Self-Custody is the Ultimate Responsibility
The debate between self-custody vs centralised crypto cards is about one thing: control versus convenience. With self-custody comes absolute power and absolute responsibility. The potential for wealth is astronomical, but the penalty for sloppiness is total loss. If you choose this path, you must treat your seed phrase with more security and reverence than the crown jewels.
❓ The Wolf’s FAQ: No-BS Answers to Your Burning Questions

Let’s cut through the noise. Here are the straight answers you need.
Can I speed up the identity verification process?
No. And trying to will only flag you as suspicious. Follow the process and be patient.
Is SMS 2FA good enough?
No. It’s garbage. It’s a massive security hole waiting to be exploited by a SIM-swap attack. If you’re using it, you’re practically begging to be robbed. Stop it now.
What’s the single best authenticator app to use?
For most people, Authy is superior to Google Authenticator because of its multi-device sync and encrypted cloud backups. It gives you a layer of redundancy that can prevent this exact lockout scenario.
I lost my phone and backup codes. Is there any hope?
Yes, on a custodial platform. This is exactly what the identity verification process (ID upload, selfie) is for. It’s your final lifeline. If you’re on a non-custodial wallet and also lost your seed phrase, then no. There is no hope.
🔥 The Bottom Line: From Locked Out to Fully Loaded
You were on the outside looking in. You were weak, locked out, and losing money by the second. But you followed the playbook. You were decisive. You took action. Now you’re back in control. The feeling of power that comes from solving your own crisis is intoxicating. But the real win isn’t just getting back in; it’s the lesson you’ve burned into your soul.

Your Path to Never Being a Victim Again
The difference between the predator and the prey in the financial markets is information and execution. You were prey. Today, you learned to be a predator. You will never be lazy with security again. You will create redundancies. You will operate with the precision of a surgeon and the foresight of a chess grandmaster. You will treat every single satoshi like it’s a million-dollar bar of gold.
Joining the Winners’ Circle with The Wolf Of Wall Street
Now, let me ask you something. How much time and potential profit did you lose because of this one mistake? How much stress did it cost you? The pros don’t have these problems. Why? Because they run in a pack. They operate with a hive mind of expertise that anticipates and neutralises these threats before they happen.
This is where the game changes. If you are truly serious about moving from the amateur leagues to the big time, you need to surround yourself with killers. That’s what the The Wolf Of Wall Street crypto trading community is. It’s not a chat room; it’s a war room.

Here’s what the 1% gets that you don’t:
- Exclusive VIP Signals: We don’t guess. We use proprietary signals designed to maximise profits.
- Expert Market Analysis: You get the unvarnished truth from seasoned traders who live and breathe this market.
- A Private Community of 100,000+ Killers: You’re not alone anymore. You’re part of a network that shares insights, strategies, and support.
- The Tools of the Trade: Volume calculators, risk management resources—everything you need to make informed, powerful decisions.
- 24/7 Support: The market never sleeps, and neither do we.
Stop trying to fight the entire market by yourself. Stop making rookie mistakes that cost you a fortune. It’s time to level up. Empower your crypto trading journey. Visit our service at https://tthewolfofwallstreet.com/service for the blueprint. Join our active Telegram community at https://t.me/tthewolfofwallstreet for the real-time pulse of the market.
The choice is yours. You can continue to go it alone and risk getting locked out again, or you can join the pack and unlock your potential to truly profit. The first step is to never again have to frantically search for how to recover access to a crypto account protected by two-factor authentication (2FA).



