Listen to me, and listen carefully. The single biggest threat to you clawing your way to the top of the crypto food chain isn’t a market crash or a bad trade; it’s the hidden danger of using pirated software. You think you’re being clever, that you’re saving a few quid on a piece of software. You think you’re gaming the system. Let me tell you something: the system is gaming you.

While you’re patting yourself on the back for that “free” download, some hacker in a dark room halfway across the world is getting ready to liquidate your entire crypto portfolio. You’re not saving money; you’re writing them a blank cheque to your future. The name of the game is wealth creation, not wealth destruction. And downloading cracked software is like pouring petrol on your portfolio and handing the matches to a stranger. It’s financial suicide.
💻 The Lure of the Forbidden Fruit: Why You’re a Target

So why do you do it? Why do smart, ambitious people who want to build generational wealth make such a fundamentally idiotic move? It comes down to one thing: a flaw in your thinking. A weakness. And in this game, weakness gets exploited by the sharks.
The Psychology of “Free”: A Flaw Hackers Exploit
The word “free” shorts out the logical part of your brain. It triggers a dopamine hit, making you feel like you’ve won, like you’ve pulled one over on the big corporations. That feeling is a drug, and hackers are the dealers. They know you crave that shortcut. They package their malware, their digital poison, inside a cracked version of that video editor or trading tool you wanted, and they wait for you to take the bait.
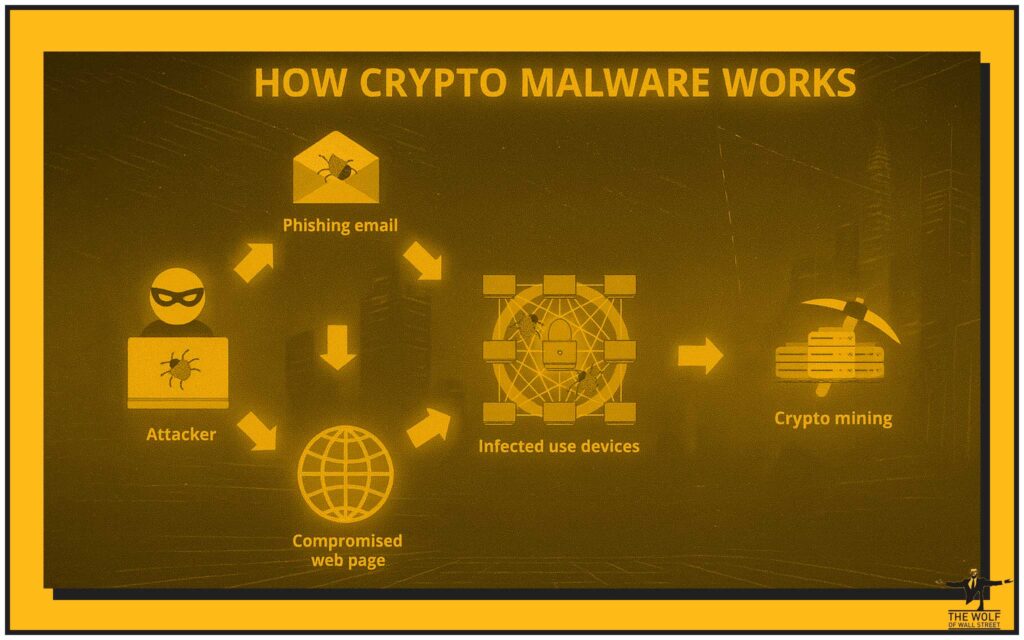
The Illusion of a Bargain, The Reality of a Heist
You see a £200 piece of software for £0. You think, “That’s a £200 win.” Wrong. That’s a potential £20,000 loss when they drain your MetaMask. It’s a £200,000 catastrophe when they get the keys to your entire exchange account. There is no bargain. It’s a trap, laid specifically for those who value short-term savings over long-term security. The most expensive thing in the world is a free lunch.
Instant Gratification, Permanent Devastation
You want the software, and you want it now. You don’t want to wait, you don’t want to pay. That impatience is a vulnerability. The internet is flooded with websites promising you exactly what you want, right this second. A few clicks, a password-protected ZIP file, and boom—you have your software. But what you really have is a Trojan Horse sitting inside your digital fortress, waiting for the right moment to open the gates and let the enemy army pour in.
The Real Cost Isn’t Money—It’s Your Future
The real cost of this mistake isn’t just the crypto they steal. It’s the time you’ll waste trying to recover. It’s the psychological blow of being violated and robbed. It’s the loss of momentum. While you’re dealing with the fallout, the winners are out there making moves, closing deals, and building their empires. You’ll be stuck at square one, all because you wanted something for nothing.
💣 Unpacking the Payload: What’s REALLY Hiding in That Cracked Software?

When you download that pirated file, you’re not just getting the programme you wanted. You’re getting a bonus package, a little something extra from your friendly neighbourhood cybercriminal. This isn’t a game; this is a hostile takeover of your digital life.
Keyloggers: The Silent Spies Stealing Your Keys to the Kingdom
This is the assassin’s blade. A keylogger is a piece of malicious code that records every single thing you type. Every password. Every private key. Every seed phrase. You type your exchange login, they have it. You type your 12-word recovery phrase into a note, they have it. It sits silently in the background, sending a perfect transcript of your secrets directly to the thief.
Remote Access Trojans (RATs): Giving Hackers a VIP Pass to Your Digital Life
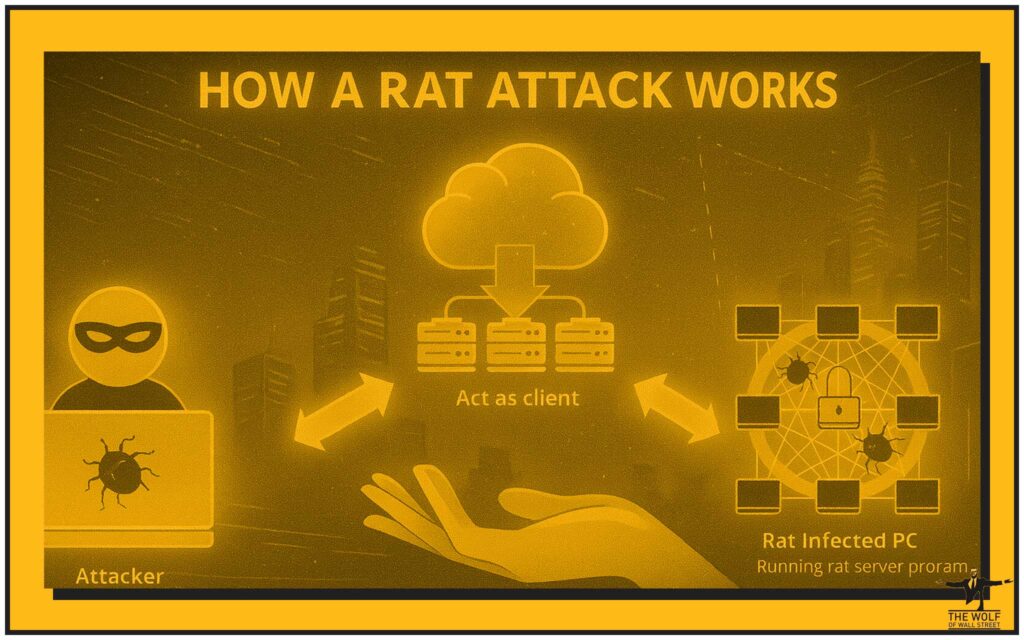
This is even worse. A RAT doesn’t just watch what you type; it gives the hacker the steering wheel to your entire computer. They can see your screen in real-time. They can open files, copy your wallet data, and even turn on your webcam. They have a front-row seat to your life, waiting for the perfect moment to move your Bitcoin from your wallet to theirs. You’re not the master of your machine anymore; you’re just a guest.
Ransomware: Your Files, Your Photos, Your Fortune—Held Hostage
Imagine waking up to find every file on your computer encrypted. Your family photos, your business documents, your crypto wallet backups—all locked away behind a password you don’t have. Then comes the demand: pay us 5 BTC in 48 hours, or it’s all deleted forever. This is digital blackmail at its most brutal. It’s delivered on a silver platter via that cracked game you couldn’t resist.
Clipboard Hijackers: The Sleight-of-Hand That Drains Your Wallet in a Blink
This one is pure, vicious genius. You copy your crypto wallet address to send funds. You paste it into the “send” field. But the malware, running invisibly, detects a crypto address on your clipboard and instantly replaces it with the hacker’s address. You glance at it—it looks right, first few characters, last few characters—you hit “Send.” And just like that, your money is gone. Forever. A simple copy-paste, a moment of inattention, and you’ve been fleeced.
🕵️♂️ The Hacker’s Playbook: A Step-by-Step Takedown of the Unsuspecting
This isn’t random. It’s a calculated, repeatable process. A sales funnel, but instead of making a sale, the product is your financial ruin.

Step 1: The Bait
Seductive Downloads on the Dark Corners of the Web
It starts on a sketchy website. A YouTube video promising a “free download link” in the description. A torrent site. A forum post. They promise you the world: the latest software, no strings attached. This is the top of their funnel.
Step 2: The Infection
How They Slip Past Your Defences Like a Ghost
The download is often a password-protected ZIP or RAR file. Why? Because it stops your antivirus from scanning the contents. They give you the password, you open it, you run the installer, and you’ve just personally invited the vampire into your home. The malware disables your security, buries itself deep in your system files, and the clock starts ticking.
Step 3: The Heist
The Silent Liquidation of Your Crypto Assets
The malware lies dormant, watching and waiting. It gathers your passwords, scans for wallet files, and monitors your activity. Then, when you’re least expecting it, the hacker strikes. They log into your accounts, bypass your alerts, and systematically drain every last satoshi. You might not even notice for hours, or days. By then, it’s too late. Your assets have been tumbled through a dozen wallets and vanished.
To beat the sharks, you have to think like them. You need to anticipate their moves. Start by learning to read the market’s pulse with tools like the MACD indicator to spot momentum signals and truly understanding the roles of Market Makers and Takers in crypto. Knowledge is power. Ignorance is ruin.
📉 Beyond the Heist: The Lingering Nightmares of Going Rogue
Even if you’re lucky enough to avoid getting your crypto stolen, using pirated software is a slow and painful poison.
Pathetic Performance & Constant Crashes: The Slow Death of Your Machine
Cracked software is unstable. It’s been tampered with by amateurs. Expect constant crashes, glitches, and system instability that kills your productivity and workflow. Your high-performance machine will run like it’s stuck in mud, all because you wanted to save a few quid.
No Updates, No Support, No Way Out
Legitimate software comes with a safety net. Security patches, performance updates, and customer support. When you go rogue, you get none of that. You are on your own. When a new vulnerability is found, you won’t get the patch. When you have a problem, there’s no one to call. You’re flying blind in a hurricane.
The Legal Hammer: Are You Prepared for the Knock on the Door?
Let’s be clear: using pirated software is illegal. It’s copyright infringement. While individual users are rarely the top priority, businesses caught using unlicensed software face crippling fines. Are you willing to risk your entire operation on a foundation of illegal activity? It’s a risk no sane entrepreneur would ever take.
🛡️ Fort Knox Your Fortune: How to Stop Being a Victim and Start Being the Bank

Alright, enough with the problem. Let’s talk about the solution. It’s time to stop acting like a sheep and start building your fortress. These are not suggestions. These are rules.
Rule Number One: Stop Playing with Fire. Buy Legitimate.
This is non-negotiable. Pay for your software. See it as an investment in your security, your productivity, and your peace of mind. If you can’t afford the tool, find a cheaper or free legitimate alternative. There are no excuses. End of story.
Armour Up: Your Non-Negotiable Security Arsenal
Get a top-tier, paid-for internet security suite. Not the free version. The real deal. Keep it updated. Run regular, full-system scans. Use a firewall. This is the bare minimum. It’s your digital bodyguard.
Cold Storage: The Unbreachable Vault for Your Crypto

If you are serious about crypto, you do not store significant amounts on an exchange or in a hot wallet on your computer. You use a hardware wallet—a cold storage device like a Ledger or a Trezor. It keeps your keys offline, away from the reach of online hackers. It’s your personal Swiss bank vault. And for God’s sake, understand the difference between your keys; our guide on the private key vs seed phrase is mandatory reading.
Two-Factor Authentication (2FA): The Digital Deadbolt That Slams the Door on Thieves
Every single account you have—exchange, email, social media—must have 2FA enabled. Use an authenticator app like Google Authenticator, not just SMS. A password alone is a welcome mat. A password plus 2FA is a reinforced steel door.
🐺 The Wolf’s Final Word: Stop Being the Sheep and Start Running the Show
Look, the world of crypto is the Wild West. It’s the greatest opportunity for wealth creation this generation will ever see. But it is filled with predators who see your ambition as their meal ticket. They prey on the lazy, the cheap, and the ignorant. Don’t be one of them. The choice is simple.

You can be the person who loses it all because they wanted a “free” video editor, or you can be the person who invests in themselves, secures their assets, and builds an empire. Stop exposing yourself to the hidden danger of using pirated software and start making decisions worthy of the future you’re trying to build.
❓ Frequently Asked Questions (FAQs)
Is ALL pirated software dangerous?
Yes. Assume every single piece of pirated software is compromised. Even if it seems to work perfectly, you have no way of knowing what’s running in the background. It’s not a risk, it’s a certainty.
Can a VPN or Antivirus really protect me if I use cracked software?
No. They help, but they are not foolproof. A VPN hides your IP address, it doesn’t stop you from installing malware. An antivirus can be disabled by modern malware. You cannot outsource your security to a tool after you’ve made a fundamentally insecure decision.
I downloaded something sketchy. What’s the first thing I should do?
Disconnect the device from the internet immediately to stop any communication with the hacker. Run multiple, different antivirus and anti-malware scans. And most importantly, move any crypto or funds accessible from that machine from a different, clean device. Assume the first machine is compromised and consider a full system wipe.
How do I know if my crypto is truly safe?
If your private keys have never touched a device connected to the internet, your crypto is safe. That’s the principle of a hardware wallet (cold storage). If your keys are on your computer or phone, your security is only as strong as the device itself.
The The Wolf Of Wall Street crypto trading community offers a comprehensive platform for navigating the volatile cryptocurrency market. Here’s what you gain:
- Exclusive VIP Signals: Access proprietary signals designed to maximize trading profits.
- Expert Market Analysis: Benefit from in-depth analysis from seasoned crypto traders.
- Private Community: Join a network of over 100,000 like-minded individuals for shared insights and support.
- Essential Trading Tools: Utilize volume calculators and other resources to make informed decisions.
- 24/7 Support: Receive continuous assistance from our dedicated support team.
Empower your crypto trading journey:
- Visit our service: https://tthewolfofwallstreet.com/service for detailed information.
- Join our active Telegram community: https://t.me/tthewolfofwallstreet for real-time updates and discussions.
- Unlock your potential to profit in the crypto market with “The Wolf Of Wall Street”.




