Listen to me, and listen closely. The crypto market isn’t a playground; it’s a battlefield. It’s a place where fortunes are made and lost in the blink of an eye. And the difference between the person driving the Lamborghini and the person crying into their pint is one thing: knowledge. Specifically, it’s understanding the single most important secret to protecting your assets: the devastating power of public and private keys in crypto.

If you don’t master this, you are gambling. You’re a chump leaving the keys to your vault lying on the table for any sharp operator to walk by and pick up. I’m here to tell you how to stop being the mark. I’m here to show you how to build a fortress around your digital wealth so that you—and only you—call the shots. Pay attention. This is the lesson that matters.
🔑 The Fundamentals: What Separates the Whales from the Minnows

Let’s cut the jargon. This is simple, but it’s profound. Get this right, and you’re already ahead of 90% of the market.
What is a Public Key?
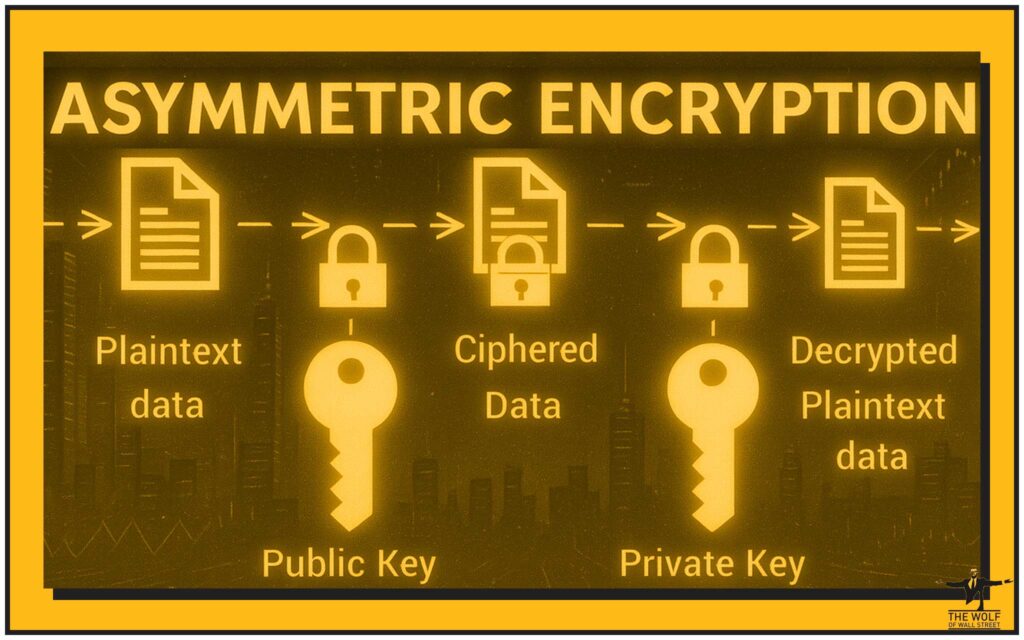
Think of your public key as the address to your digital mansion. It generates a public address—a string of letters and numbers—that you can hand out to anyone.
Your Public Address: The Mailbox for Your Millions
When someone wants to send you Bitcoin, Ethereum, or any other coin, you give them your public address. It’s like giving someone your bank account number and sort code. It’s public information. People can send money to it, but they can’t use it to take a single penny out. You can plaster it on a billboard if you want; it doesn’t matter. It’s a one-way street, designed to get you paid. Simple.
What is a Private Key?
Now, this is the big one. This is the holy grail. The private key is a secret, cryptographic code. It is absolute proof of ownership. It is the one and only thing that gives you the power to access and control the crypto in your wallet.
The God Key: Your Absolute Control Over Your Fortune
If your public key is the address of the vault, your private key is the only key that opens the door, turns off the alarms, and gives you access to the gold inside. Whoever holds this key, holds the coins. It’s not tied to your name, your passport, or your company. It is pure, absolute, mathematical control. You hold it, you own it. You lose it, you lose everything. Someone else gets it, they own everything. There is no middle ground.
The Golden Analogy: The Bank Account vs. The Vault PIN
- Public Key: Your IBAN or bank account number. Share it to get paid.
- Private Key: The PIN code to your bank card. The password to your entire net worth. You wouldn’t write your PIN on a Post-it note and stick it to your forehead, would you? You keep it secret. You keep it safe. You never, ever, let it out of your sight.
📜 The Origin Story: Where Did This Power Come From?

This technology wasn’t just invented yesterday. It’s born from decades of high-level cryptographic genius. Understanding where it came from shows you just how rock-solid it is.
The Geniuses Behind the Curtain: Diffie & Hellman
Back in the 1970s—long before crypto was a word—two visionaries named Whitfield Diffie and Martin Hellman cracked a problem that had stumped spies and governments for centuries: how can two people share secret information without first meeting to exchange a secret key? They invented public-key cryptography, and the game was changed forever.
The Evolution of Power: From RSA to Elliptic Curve Cryptography (ECC)
What Diffie and Hellman started, others perfected. Algorithms like RSA and, more importantly for crypto, Elliptic Curve Cryptography (ECC), made the process leaner, meaner, and more secure. Bitcoin, Ethereum, and the vast majority of other cryptocurrencies are built on this battle-tested foundation.
Why This History Matters to Your Bottom Line
Why am I telling you this? Because you need to know that the security of your assets isn’t based on wishful thinking. It’s based on mathematical principles that are so strong, the most powerful computers in the world can’t break them. The system is strong. The weak link is always the person holding the key—you.
⚙️ How It All Works: The Engine of Your Crypto Empire
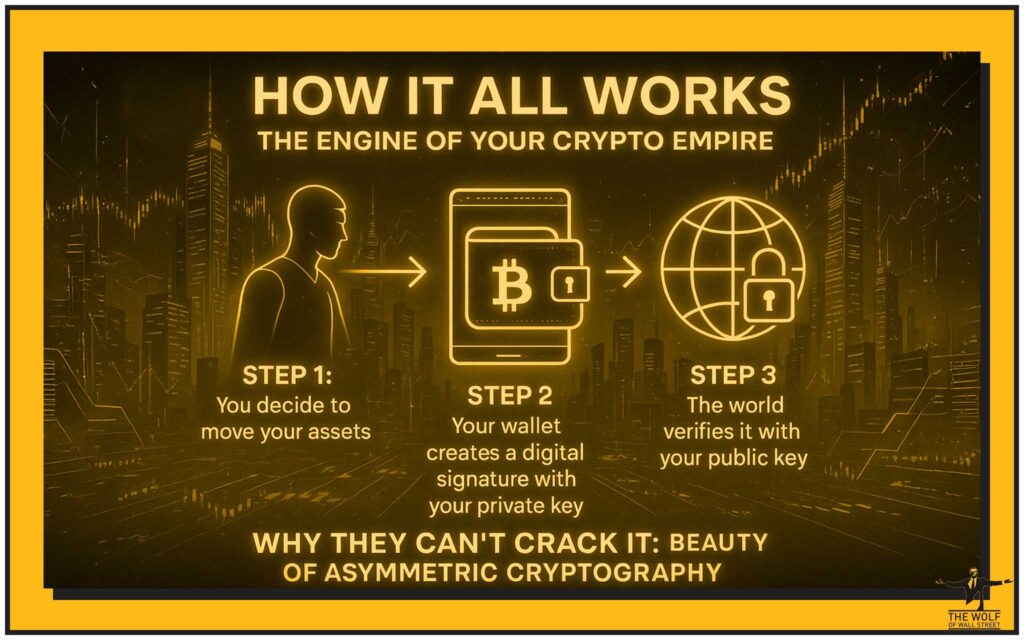
So how does this dance between two keys actually move your money? It’s a beautiful, elegant process.
The Transaction: A Step-by-Step Playbook
When you decide to send your crypto, you’re not actually “sending” files. You’re signing a message on a public ledger. Here’s how it goes down.
Step 1: You Decide to Move Your Assets
You open your wallet and input the recipient’s public address and the amount you want to send. You hit ‘Send’. The game is on.
Step 2: Your Wallet Creates a Digital Signature with Your Private Key
This is the magic. Your wallet software takes the transaction details and uses your private key to create a unique digital signature. This signature is a mathematical seal of approval. It proves you, and only you, authorised this transaction.
Step 3: The World Verifies it with Your Public Key
The transaction, along with your digital signature, is broadcast to the network. Everyone on the network can then use your public key to verify that the signature is authentic. They can see the signature was created by the corresponding private key, but they can never see the private key itself. If it verifies, the transaction is confirmed and added to the blockchain. Your money has moved.
Why They Can’t Crack It: The Beauty of Asymmetric Cryptography
The keys are mathematically linked, but it’s a one-way street. It is trivial to generate a public key from a private key, but it is practically impossible to reverse the process. It would take all the computing power on Earth billions of years to guess your private key from your public one. That’s the power of asymmetric cryptography.
🛡️ Security: This Is Where 99% of People Fail (Don’t Be One of Them)

Do not get comfortable. The system is secure, but people are weak. This is where the wolves separate from the sheep. Security is not a suggestion; it’s a religion.
Your Private Key Is YOURS. Period.
I’ll say it again. Never share your private key. Not with a support agent, not with a “wallet upgrade” site, not with your dog. Any person or platform asking for your private key is a scammer, 100% of the time. End of story.
Introducing the Seed Phrase: Your Ultimate Backup Plan
Your private key is a long, complex string of characters. It’s a nightmare to handle. That’s why modern wallets use a “seed phrase” or “mnemonic phrase”—a list of 12 to 24 simple words.
What it is and Why it’s Your Lifeline
This phrase is your master key. From this one phrase, your wallet can regenerate every single private key and public address you will ever use. If your phone falls in the ocean or your laptop explodes, you can download a new wallet, enter your 12 words, and boom—your entire crypto portfolio is back. But don’t get it twisted; this phrase is even more sensitive than a single private key. Anyone who has it has everything. Knowing the difference is crucial; it’s why you must understand the relationship between a private key vs seed phrase.
The Wallet Game: Are You Playing it Right?

Not all wallets are created equal. Where you store your keys determines your level of risk.
Hot Wallets vs. Cold Wallets: The Trade-Off
- Hot Wallets: These are connected to the internet (desktop, mobile, web wallets). They are convenient for daily transactions but are more vulnerable to online attacks.
- Cold Wallets (Hardware Wallets): These are physical devices that store your keys offline. They are the gold standard for security. Your keys never touch the internet, making them immune to hacking.
Serious players keep the bulk of their assets—their long-term holds—in a cold wallet. They only keep “walking around money” in a hot wallet.
🏆 The Wolf’s Rulebook: Best Practices for Key Management

Follow these rules religiously. No exceptions. This is your code.
- Rule #1: Use Hardware Wallets for Serious Holdings. Get a Ledger or a Trezor. It’s non-negotiable for any amount of money you can’t afford to burn.
- Rule #2: Enable Two-Factor Authentication (2FA) Everywhere. On your exchange accounts, your email, everything. Use an app like Google Authenticator, not just SMS.
- Rule #3: Keep Your Software Updated. Wallet updates contain critical security patches. Don’t be lazy.
- Rule #4: Master the Art of Spotting Phishing Scams. Triple-check URLs. Be paranoid about emails and DMs. Scammers are sharks, and they smell blood in the water.
- Rule #5: Use Strong, Unique Passwords. Don’t reuse passwords. Use a password manager to create and store cryptographic-level passwords.
- Rule #6: Write Down Your Seed Phrase. Store it Offline. In Two Places. Never store it as a digital file on your computer or phone. Write it on paper, stamp it in steel, and store it in secure, separate locations.
- Rule #7: Consider Multisignature Wallets for a Fortress of Security. For serious assets, a multisig wallet requires multiple keys to authorise a transaction. Amateurs use one key. Professionals are looking at concepts like multi-party computation for crypto security to build financial fortresses.
❓ Frequently Asked Questions (The Stuff Rookies Ask)
Let’s clear the air on a few common points of confusion.
What’s the main difference between public and private keys?
The public key is for receiving; you can share it freely. The private key is for sending; you must guard it with your life.
Can I get my private key back if I lose it?
No. If you lose your private key and you haven’t backed up your seed phrase, your money is gone. Forever. There is no customer support line to call. You are your own bank.
How do I know if my wallet is secure?
Security comes from the source. Use well-known, open-source wallets. For ultimate security, a hardware wallet is the only answer.
Why can’t I just memorise my private key?
Because you’re human. Private keys are long and complex. A seed phrase is easier, but still, don’t rely on memory alone. Mistakes will cost you everything. Write it down.
⚡ Conclusion: You Now Have the Keys – It’s Time to Unlock Your Fortune

You’ve made it to the end. Now you know the secret. You understand the lock, and you hold the key. The power dynamic in the crypto world is crystal clear: it’s divided between those who control their keys and those who let others control them. You are now in the first group. You have the knowledge to protect your assets like a professional, to build your wealth on a foundation of rock-solid security, and to operate with the confidence of a true market player. This is the bedrock. From here, you can go on to master crypto order types for trading and execute your vision with precision.
But knowledge alone isn’t enough. The best traders in the world, the real wolves, run in a pack. They operate with an edge.
Empower Your Crypto Trading Journey with The Wolf of Wall Street’s Crypto Community (The Wolf Of Wall Street)
You have the foundation. Now it’s time to join the inner circle. The The Wolf Of Wall Street crypto trading community is a comprehensive platform for navigating the volatile cryptocurrency market. This is what you get when you run with us:

- Exclusive VIP Signals: Stop guessing. Get access to proprietary signals engineered to maximise your trading profits.
- Expert Market Analysis: Let our seasoned crypto traders give you the in-depth analysis you need to make killer decisions.
- Private Community: Join a network of over 100,000 wolves. Share insights, strategies, and win together.
- Essential Trading Tools: Use our volume calculators and other critical resources to trade with an unfair advantage.
- 24/7 Support: Our team is always there to back you up.
Stop playing in the minor leagues. It’s time to unlock your true potential to profit.
- Visit our service for more details: https://tthewolfofwallstreet.com/service
- Join our active Telegram community for real-time action: https://t.me/tthewolfofwallstreet
You now understand the critical importance of public and private keys in crypto; the next step is to use that power effectively.



